Why I Wrote This
Over the years, I’ve worked on multiple modernization efforts across enterprise and public-sector systems. In that time, I’ve seen how legacy applications quietly slow delivery, strain teams, and limit what agencies can realistically provide to citizens. This article isn’t theoretical. It captures the architectural patterns and lessons that have consistently worked in real government modernization efforts, especially in environments where risk, compliance, and continuity matter more than chasing trends.
For most of my career, I’ve walked into government IT rooms where the first thing you notice isn’t the technology — it’s the tension. A system built twenty or thirty years ago is still running critical programs. Everyone knows it needs to evolve, but no one wants to be the person who touches the wrong line of code and brings down an entire agency.
Legacy systems don’t fail loudly.
They fail slowly.
A small policy update takes months to implement.
A new security requirement breaks a module that hasn’t been touched in years.
A spike in citizen traffic causes the system to freeze at the worst possible moment.
A new developer joins the team and spends weeks just trying to understand where everything lives.
After seeing this pattern repeat across multiple agencies, I realized something important:
modernization isn’t just a technical upgrade — it’s an architectural reset.
Where Modernization Really Begins
Most legacy systems share the same underlying problem: everything is tightly coupled.
The UI, business logic, and data access are woven together like old wires in a basement.
Pull one, and you risk pulling them all.
You can’t modernize a system like that by swapping out a framework or rewriting a few screens.
You have to rethink how the system is structured.
That’s where a layered, domain‑centric approach comes in — not because it looks good in a diagram, but because it actually works in real modernization projects.
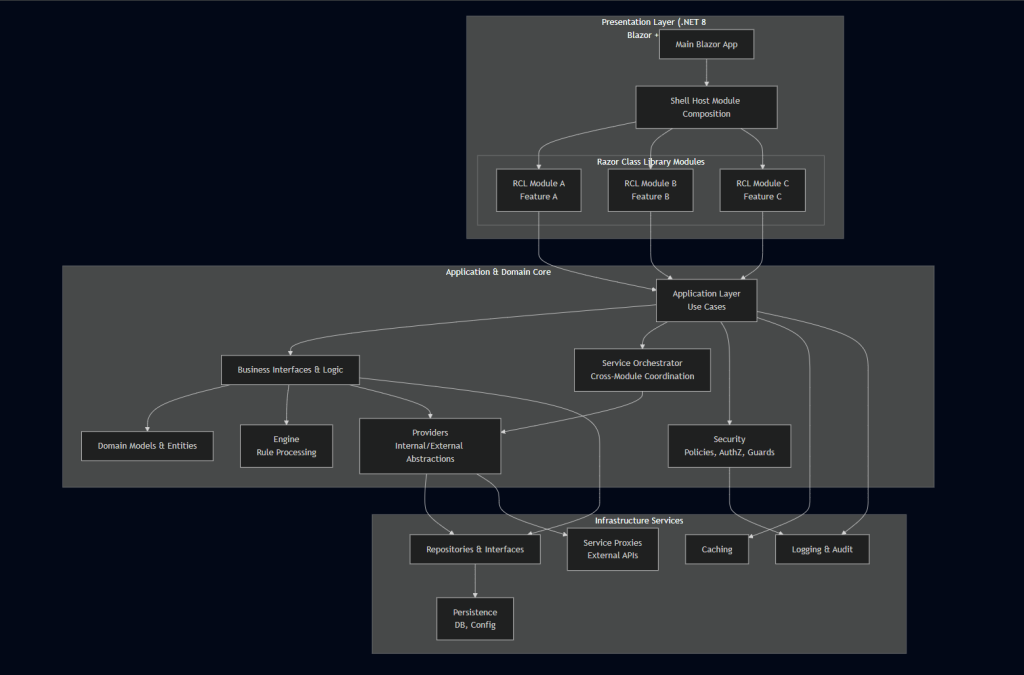
A Practical, Layered Architecture That Holds Up Over Time
The architecture that consistently succeeds in government modernization breaks the system into three major layers:
- Application & Domain Core
- Infrastructure Services
- Presentation Layer (Blazor + Modular RCLs)
Each layer has a clear purpose.
Each layer evolves independently.
And together, they create a foundation that can support the next decade of government needs.
- The Domain Core: The Heart of the System
- This is where the real business rules live — the decisions, workflows, and logic that define how the agency operates.
- Inside the core, everything has a clear role:
- Application Layer – Coordinates workflows and use cases
- Business Interfaces & Logic – Defines and enforces rules
- Domain Models & Entities – Represents real-world concepts
- Engine – Handles reusable rule processing
- Providers – Abstracts internal and external dependencies
- Service Orchestrator – Manages interactions across modules
- Security – Centralized authorization and policy enforcement
- When this layer is clean and well‑structured, everything else becomes easier — testing, onboarding, scaling, and adapting to policy changes.
- The Infrastructure Layer: The Quiet Workhorse
- If the domain core is the brain, the infrastructure layer is the nervous system, It handles:
- caching
- logging and audit trails
- database access
- repository patterns
- external service integrations
- These are the things no one notices when they work — and everyone notices when they don’t.
- By isolating them, you make the system easier to secure, audit, and migrate to the cloud.
- The Presentation Layer: Where Blazor and RCLs Change the Game
- This is where modernization becomes visible.
- Instead of one giant UI, each feature becomes its own modular Razor Class Library:
- self-contained
- independently deployable
- easy to test
- easy to evolve
- The structure usually includes:
- Main – the entry point
- Client – client-side logic (if needed)
- Shell – the host that brings all modules together
- This modular approach lets teams work in parallel without stepping on each other’s code.
- It also prevents the UI from becoming another monolith.
Security: Woven Into Every Layer
Government systems can’t afford to treat security as a checkbox.
In this architecture, security is built into every layer:
- centralized identity
- policy-based authorization
- secure middleware pipelines
- structured logging
- layered validation
It’s not just about compliance — it’s about building trust into the system itself.
What Agencies Gain From This Approach
When teams adopt this architecture, the results are noticeable:
- new features ship faster
- the system scales more reliably
- onboarding becomes easier
- technical debt drops
- security posture improves
Most importantly, agencies gain the confidence to evolve their systems without fear of breaking everything.
Why This Matters Beyond a Single Project
This isn’t a one-time solution.
It’s a blueprint.
I’ve seen it work across:
- state systems
- federal platforms
- compliance-heavy enterprise applications.
Closing Thoughts
Modernizing legacy systems isn’t about chasing the newest framework.
It’s about building an architecture that respects the past while preparing for the future.
.NET 8, Blazor, and modular RCLs offer a practical, future-ready way to do exactly that — not just for one agency, but for any public-sector system that needs to evolve with the world around it.